
Home is where we should feel safe.
OK, so our homes have lately been threatened by fire and flood, but they should still be our place of refuge.
Unfortunately, with the development of 24/7, all-access digital technology, many homes are the places where significant emotional and financial damage occurs.
Two of the most pervasive dangers come from:
- Cyberbullying: Thisincludes sending, posting, or sharing negative, harmful, false, or mean content about someone else. It can include sharing personal or private information about someone else causing embarrassment or humiliation. Some cyberbullying crosses the line into unlawful or criminal behaviour.
- Phishing: These are online attacks that are based on sending fraudulent communications that appear to come from a reputable source. It is usually done through email. The goal is to steal sensitive data like credit card and login information, or to install malware on the victim’s machine. Sometimes attackers are satisfied with getting a victim’s credit card information or other personal data for financial gain. Other times, phishing emails are sent to obtain login information or other details.

If a young person or adult is being bullied at school or in the workplace, digital technology means that the bully/bullies can “follow” them home. The attacks do not stop at the front door.
“When Russia invaded Ukraine Australians recoiled in horror at the shameless bullying of a geopolitical giant against a vulnerable neighbour with whom it lived cheek by jowl. The decent nations of the world rightly condemned such an act and moved swiftly to punish the perpetrator. And yet here in our own neighbourhoods, our own homes, such acts of bullying are going on every day — and also with deadly consequences. This was brought into sharp and tragic relief with the death of Tilly Rosewarne, a 15-year-old girl from Bathurst who committed suicide after years of abhorrent bullying on the social media platform Snapchat. Yet another young soul has been lost thanks to the torrent of abuse and torment that is now able to be transmitted 24/7 with ruthless efficiency by multinational tech giants.” The Australian
Cyberbullying behaviour might include:
- abusive texts and emails;
- hurtful messages, images or videos;
- imitating others online;
- excluding others online;
- humiliating others online;
- spreading nasty online gossip and chat;
- creating fake accounts to trick someone or humiliate them.
The effects of cyberbullying include mental health issues, increased stress and anxiety, depression, acting out violently, and low self-esteem. Cyberbullying can also result in long-lasting emotional effects, even if the bullying has stopped. Sometimes it can result in death.

If you haven’t been the victim of a cyberbullying attack, consider yourself fortunate because:
- 1 in 5 Australian young people reported being socially excluded, threatened or abused online;
- 55% sought help from their parents, 28% from their friends; 38% blocked the offending social media account; 12% reported it to the website or platform;
- 1 in 5 Australian young people (15% of kids, 24% of teens) have admitted behaving in a negative way to a peer online — such as calling them names, deliberately excluding them, or spreading lies or rumours. Of these, more than 90% had had a negative online experience themselves.
Here are some strategies if you are cyber-attacked:
- Ignore. Sometimes bullies are encouraged by seeing a reaction.
- Record. Keep a record of bullying messages you receive—in hard copy. If you can show an adult either the messages themselves or a diary of when you received them, it may be easier to verify what went on and who the bully was.
- Reach out. Your parents, a favourite teacher and even police officers can help you deal with cyberbullying.
- Cut off the bully. Stop all communication with the bully when possible. Block their phone number so you no longer receive their calls or texts.
- Go high-tech. If you’re being bullied via a website, chances are that the bully is going against the website’s terms of use. Reporting bullies to the website administrator may get them kicked off the site.
What Not to Do
- Sink to the bully’s level.
- Forward bullying content or messages.
- Believe the bully.

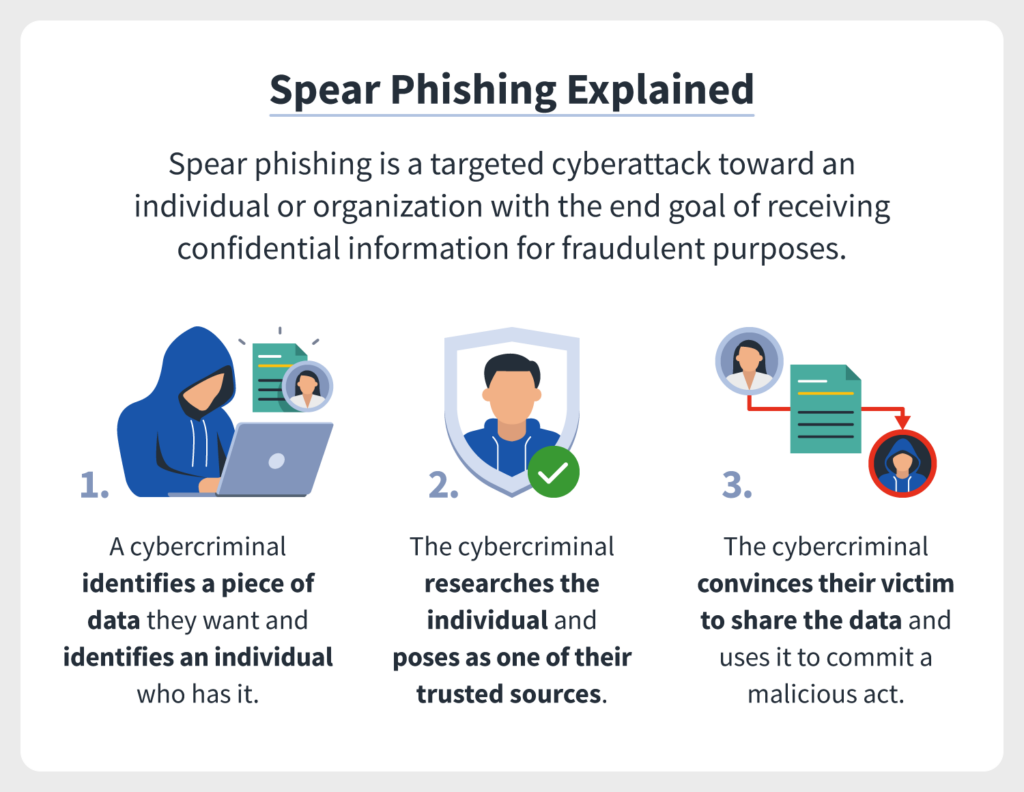
The other increasingly dangerous digital phenomenon comes in the form of phishing. Although phishing strategies constantly evolve, the most common forms are:
1. The Fake Invoice Scam: Like many phishing attacks, this scam relies on fear and urgency, pressuring an end user to submit a payment for goods or services they’ve never even ordered or received. Not that common for adolescents, more for finance departments.
2. Email Account Upgrade Scam: Faced with having your account expire unless immediate action is taken, the email account upgrade scam can appear to come from trusted email providers like Microsoft and Google, or simply from your company’s IT department. A useful tip is to hover over the link itself when being asked to give personal details – as the text itself often doesn’t represent the true destination of the link.
3. Google Docs Scam: One of the more recent high-profile phishing techniques, the Google Docs scam encourages you to click on its link in order to view a ‘document’, which then takes you to an almost identical version of Gmail’s login page. Once an account has been selected, you’re then invited to grant access to your Google account, meaning the attacker has free rein.
4. PayPal Scam: PayPal is an incredibly lucrative tool for a cyber criminal. As well as its high volume of accounts, PayPal offers fraudsters the chance to take advantage of a platform linked directly to your credit card or bank account. These emails often include the PayPal logo, plus a convincing chunk of fine print at the bottom of the email. Again, this scam tries to enforce panic mode into its victims, often with a “There’s a problem with your account, please click here to fix it” kind of message. Beware, they also contain legitimate-looking fine print.
5. Unusual Activity Scam: When receiving an email or text stating that there has been “suspicious activity on your account”, your alarm bells start ringing at full pace. That’s why this scam works so well for scammers, as victims aren’t just faced with urgency and panic – they’re also faced with confusion.
Almost all phishing strategies play the card of emotions to trick users into clicking on links or responding to information requests by creating a sense of urgency. This works well with teens who are more likely to act on impulse more than other age groups.

The ACCC’s Scamwatch website helps you learn how to recognise, report and protect yourself from scams. Scamwatch contains information for consumers and small business including:
- the most common scams
- victims’ stories
- golden rules to protect yourself
- email alerts
- where to report a scam
What have you got to lose from phishing?
- Your identity;
- Your money;
- Your dignity.
Be aware, be safe.

Terry Muldoon
Principal
Want to share your thoughts on this story, or do you have something you’d like to add? Email me at principal@scas.nsw.edu.au

